| ☰ See All Chapters |
AWS Identity and Access Management (IAM)
Identity and Access Management, referred to as IAM is a central part to closely control exactly who and what can access your resources. Or, in other words, how to secure your AWS account. In this chapter, we will demonstrate how we can create and administer IAM users, groups, roles, and policies using AWS Management Console, AWS CLI, AWS SDK – Java, and CloudFormation.
When it is large project, a single person cannot handle and administrate everything, you may need to hire a few developers or some devops engineer professionals. Now all these developers and devops engineer should be granted with access to reach AWS services, in this case to limit the exposure to risk, security best practices recommend permitting each user access to no more than they absolutely require. So you’ll have to find a way to finely tune how people get through your front door. This access management is done through AWS access management.
To provide granular-level permissions to users or AWS resources to access other AWS resources, AWS has provided below four account authentication configurations.
Users
Policies
Groups
Roles
Users
Each user owns an account in AWS and use their own access credentials to gain access to the resources permitted by group policies.
Policies
The core of everything is the IAM policy, which defines exactly who may perform which actions on what resources. A Policy is a JSON document that contains a list of permissions to allow or deny access to AWS resources. A single policy can be attached to one or more IAM user, group, and role.
"Version": "2022-02-21", "Statement": { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::9041-1945-7762:user/manu" }, "Action": [ "s3:PutObject", "s3:PutObjectAcl" ], "Resource": "arn:aws:s3:::devopsteam/*" } } |
You can use AWS Visual editor to configure policies, so you not necessary to remember and understand the different parts of JSON. Visit below link to create or edit policy:
https://console.aws.amazon.com/iam/home#/policies$new?step=edit
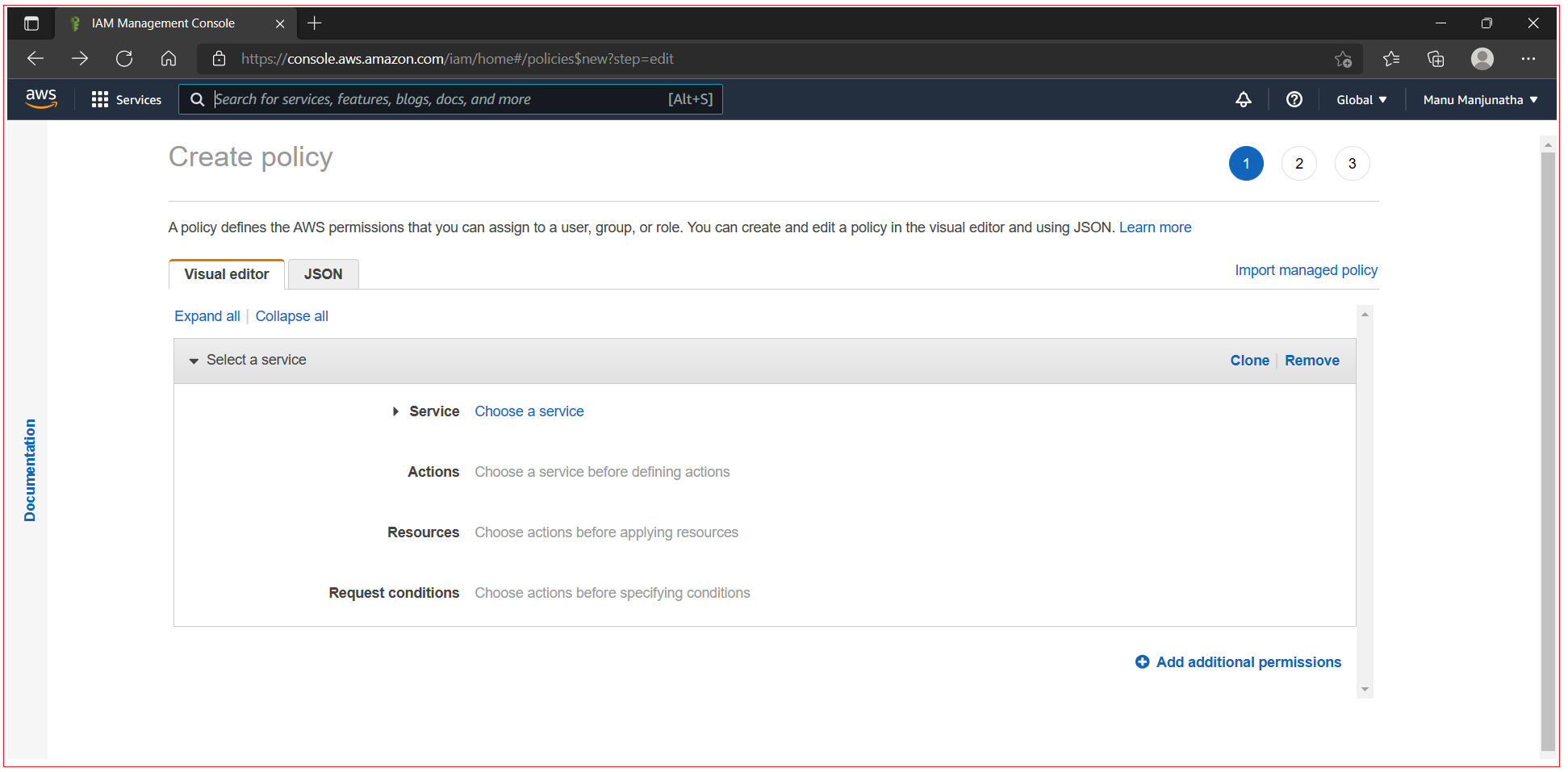
Groups
You can combine multiple policy and from a group of policies this can be associated with IAM users. So, when we create an IAM user, and associate it with a group, it means the user can get access to all the AWS resources mentioned in the group's policies. It becomes easier to provide and manage access based on groups. If a user moves from one business group to another in the same organization, the administrator will only change the group assignment for a particular user.
Groups don’t have their own access credentials. Instead, any users who’ve been added to a group will use their own credentials to gain access to the resources permitted by group policies.
Using groups you can manage permissions to users easily, rather than defining and frequently updating complicated policies for each user, you can update the group policies, and all of its members will automatically inherit the changes. This way, for instance, adding a new developer to the system will only require that you create a single new user account and then add it to your preexisting group.
Roles
A role is an identity that has specified restrictions and permissions assigned to objects like EC2 instances and applications. You can create different roles like administrator, manager, moderator, developer role etc.. Developers will be assigned with developer roles where this role has privileges set to no more than absolutely what developers require.
All Chapters

